Wardriving is the art of executing a mobile attack surface, by literally being on the move while propagating a wireless attack. You achieve this by creating an enhanced environment within a vehicle to avoid geolocation detection.
The goal is to take advantage of open wireless networks to prey upon unsuspecting victims – in locations such as hotels, coffee shops, airports, etc. The image below depicts a coffee shop and everything looks “normal”.

You can see the coffee shop, patrons’ vehicles, and a white panel van. Nothing looks suspicious, so let’s take a closer look.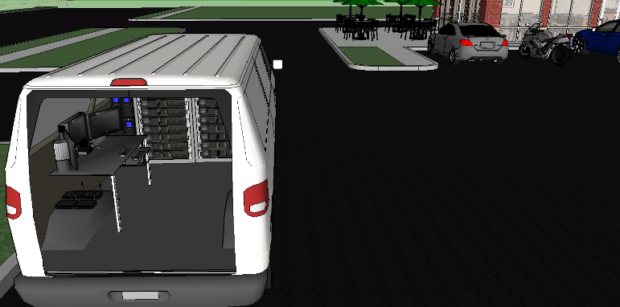
[Removing the back doors for visibility purpose] We can now see that the inside of this seemingly innocent van. There is a plethora of network equipment, ample power supplies for mobile sustainability, computers, wireless peripherals, and it’s all hidden within this vehicle.
This example looks exaggerated, but government funded APTs can easily achieve this attack methodology. I’ve personally performed a similar attack vector working as part of a red team (as a sanctioned and strictly defined scope approved by the client of the engagement) – landing a drone on the roof of the victim building to plant an ‘evil twin router’ within intercept distance of victim laptops; with the goal of stealing pre-shared keys.
This well-crafted attack vector is highly effective as you can sit in plain sight with LoS (line of sight) to your victims – for enhanced signal strength during the attack.
Ultimately, the likely yield is to duplicate the SSID of the AP at the establishment, to MITM (man-in-the-middle) traffic to capture credentials. Often, patrons perform nefarious activities on open wireless networks – such as online banking, checking personal or work emails, signing in to social media services, etc.
Security Awareness plays a huge role in protecting against this type of attack, coupled with advanced technologies to identify attack vectors such as this one. Using tools that perform rogue AP sniffing, SSID counter-spoofing monitoring, endpoint protection, and mobile defense frameworks will ultimately protect the would-be victim. Unfortunately, rarely any of these tactics are employed today and thus leaves the vast majority of users vulnerable when they least suspect it.
We must be vigilant, we must be ready, and most of all, we must be educated!

Adam Zimmerman, Security Solutions Architect
CDW Canada
With over six years of experience in the technology industry, Adam’s experience covers information security operations, cyber security advisory, penetration testing, and advanced exploitation. Adam’s primary focus is helping organizations build strong security practices and prepare for potential attacks.
Adam holds a Masters in IT Security from the University of Ontario Institute of Technology, where he successfully developed a malware classification tool with a security firm based in Ottawa. Additionally, he has worked on several cyber consulting engagements as a lead security researcher and was able to develop an exploit for the FAA’s NextGen Air Traffic Control Management System.
Adam currently serves in the Canadian Armed Forces as a Second Lieutenant where he holds a command position as a Troop Commander for 32 Combat Engineer Regiment of Toronto; specializing in mobility denial and facilitation, tactical breaching, controlled munitions disposal, and various humanitarian support operations.







