Secure Socket Layer [SSL] certificates were first used in the early 90’s and have since grossed over 2 trillion dollars via enabling e-commerce sales. In the market, today, SSL certificates [certs] are used to apply levels of security to the plaintext HTTP protocol – you would see a small green lock symbol to denote ‘HTTPS in use’.
The industry is very focused on ensuring a well-trusted Root Certificate Authority is creating the certs we buy that ultimately control the level of encryption that governs the cert (and traffic to/from the registered domain). Considering there are several different classifications of HTTPS certs, the green lock symbol doesn’t denote which one is in use nor the actual grade of encryption governing traffic to that domain. Thus, we need to understand the common types of SSL certs – see below;
- Domain Validated Certificate [DV] – commonly used by hackers because the domain certification will appear more safe than it is, this utilizes the lowest grade SSL encryption. DV certs are often governing landing pages of phishing emails so they look legitimate and play upon social engineering weaknesses of victims.
- Organizationally Validated Certificate [OV] – To generate and receive this cert, many pieces of information are required as they are registered with the certificate; organization/company name, geolocation, and the domain name.
- Extended Validation Certificate [EV] – This cert has the greatest encryption of all three certificate classifications. A governing body is required for the issuing process of EV certs and a deep inspection of the requesting entity is performed; down to business records and applicant identity checks.
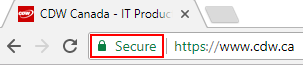
I![]() t can be seen in this image that “The Toronto-Dominion Bank” is written in green letters in addition to the lock symbol. This is the difference between an EV cert vs. DV & OV certs. DV & OV certs will both appear identical in the search bar and is impossible to determine unless you inspect the certificate before using the website. Considering the average user will not perform this inspection, it is very easy to raise the level of security awareness of employees to look for the EV type certificates and have a sense of distrust if the formatting doesn’t match.
t can be seen in this image that “The Toronto-Dominion Bank” is written in green letters in addition to the lock symbol. This is the difference between an EV cert vs. DV & OV certs. DV & OV certs will both appear identical in the search bar and is impossible to determine unless you inspect the certificate before using the website. Considering the average user will not perform this inspection, it is very easy to raise the level of security awareness of employees to look for the EV type certificates and have a sense of distrust if the formatting doesn’t match.
Ideally, larger [trusted] organizations will all move to EV certs and this will become the new standard – this would drastically counter phishing campaigns and make it much more difficult to social engineer via online medium.
We must be vigilant, we must be ready, and most of all, we must be educated!

Adam Zimmerman, Security Solutions Architect
CDW Canada
With over six years of experience in the technology industry, Adam’s experience covers information security operations, cyber security advisory, penetration testing, and advanced exploitation. Adam’s primary focus is helping organizations build strong security practices and prepare for potential attacks.
Adam holds a Masters in IT Security from the University of Ontario Institute of Technology, where he successfully developed a malware classification tool with a security firm based in Ottawa. Additionally, he has worked on several cyber consulting engagements as a lead security researcher and was able to develop an exploit for the FAA’s NextGen Air Traffic Control Management System.
Adam currently serves in the Canadian Armed Forces as a Second Lieutenant where he holds a command position as a Troop Commander for 32 Combat Engineer Regiment of Toronto; specializing in mobility denial and facilitation, tactical breaching, controlled munitions disposal, and various humanitarian support operations.







