To exist as an organization in the information era, you need to be available to the masses via the internet. As such, you require to be accessible online via a hosted website (and web applications) which are either a third-party service or in-house hosted.
Today, the most publicized breaches have occurred due to the lack of adhering to industry best practice as it pertains to web application security standards. The first line of defense is to ensure that your online exposure is reduced by avoiding any reputational loss. Meaning, if your web server (and/or web app) succumbs to a logic breach, the contents and availability of the hosted environment can be altered or removed.
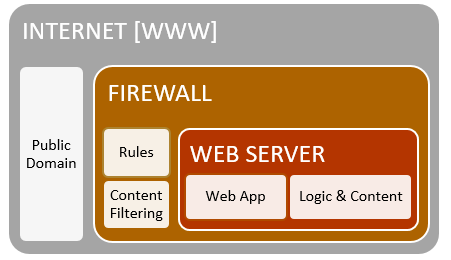
Reference the image above, the web server traditionally sits in an insulated environment that is behind a firewall. This is due to the content & administration components involved in hosting the service.
If you can successfully manipulate [then compromise] the web server, you can obtain a foothold on the victim’s environment. As you can see, the web server is an authenticated node on the network – thus a great pivoting attack vector for hackers if the attack is successful.
Looking at some breaches of late, a large credit union was compromised via the web server and thus sensitive information was siphoned from the internal environment. The web server was used as an exfiltration point because of the lack of security hardening activities that should have taken place. There are many security standards to look to for guidance, including penetration testing.
Web application penetration testing can vastly reduce your overall attack surface, as trained cyber security professionals will attempt to circumvent web logic and web server functionality to create unforeseen subroutines of the web server. This will expose weaknesses and thus help identify vulnerabilities that can be patched to avoid the calamity of a substantial data breach.
We must be vigilant, we must be ready, and most of all, we must be educated!
If you missed part two of this series you can catch up here!

Adam Zimmerman, Security Solutions Architect
CDW Canada
With over six years of experience in the technology industry, Adam’s experience covers information security operations, cyber security advisory, penetration testing, and advanced exploitation. Adam’s primary focus is helping organizations build strong security practices and prepare for potential attacks.
Adam holds a Masters in IT Security from the University of Ontario Institute of Technology, where he successfully developed a malware classification tool with a security firm based in Ottawa. Additionally, he has worked on several cyber consulting engagements as a lead security researcher and was able to develop an exploit for the FAA’s NextGen Air Traffic Control Management System.
Adam currently serves in the Canadian Armed Forces as a Second Lieutenant where he holds a command position as a Troop Commander for 32 Combat Engineer Regiment of Toronto; specializing in mobility denial and facilitation, tactical breaching, controlled munitions disposal, and various humanitarian support operations.







